Search Exchange
Search All Sites
Nagios Live Webinars
Let our experts show you how Nagios can help your organization.Login
Directory Tree
check_fail2ban
Current Version
1.1
Last Release Date
2013-02-22
Compatible With
- Nagios 1.x
- Nagios 2.x
- Nagios 3.x
- Nagios XI
- Nagios Fusion
Owner
License
GPL
Hits
49281
Files:
| File | Description |
|---|---|
| check_fail2ban.sh | check_fail2ban.sh |
checks for banned IP's
integrated performance data for banned IPs
shows banned IP since the last logrotate in long output
Modified:2013-03-12 (version 1.1)
-fix wrong count for output
-implement status check
Reviews (2)
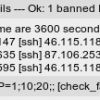
In the header block it mentions a staus check being implemented which I think is where this came from at line 18
ps_state=$(ps aux |grep "fail2ban.sock" |grep -v grep| wc -l)
This seems to be an attempt to check if the fail2ban.sock socket has been created by the nagios-server, except this is looking at processes not sockets or at least it is on my Centos 7.7 installation, it always returns zero so the program aborts further down with the message
++++ Process is not running ++++
Change line 18 to this instead
ps_state=$(ss -aux |grep "fail2ban.sock" |grep -v grep| wc -l)
Basically use ss instead of ps and put the - before the aux
options.
Then it returns 1 as expected if the fail2ban-server is running and the script works correctly.
ps_state=$(ps aux |grep "fail2ban.sock" |grep -v grep| wc -l)
This seems to be an attempt to check if the fail2ban.sock socket has been created by the nagios-server, except this is looking at processes not sockets or at least it is on my Centos 7.7 installation, it always returns zero so the program aborts further down with the message
++++ Process is not running ++++
Change line 18 to this instead
ps_state=$(ss -aux |grep "fail2ban.sock" |grep -v grep| wc -l)
Basically use ss instead of ps and put the - before the aux
options.
Then it returns 1 as expected if the fail2ban-server is running and the script works correctly.
bysvamberg, September 13, 2016
1 of 2 people found this review helpful
Output of 0.9.x fail2ban is different (added white characters). This patch fix it:
--- a/check_fail2ban.sh
+++ b/check_fail2ban.sh
@@ -105,7 +105,7 @@ fi
# #####################################################################
# Run the fail2ban-client, and generate the list of operating jails
# #####################################################################
-jail_list=$($fail2ban_client status|grep "list" |cut -f 3 |tr -d ,)
+jail_list=$($fail2ban_client status|grep "list" | cut -d : -f 2 | tr -d ,)
# #####################################################################
# Cycle through all jails, count blocked IP, and build output strings
--- a/check_fail2ban.sh
+++ b/check_fail2ban.sh
@@ -105,7 +105,7 @@ fi
# #####################################################################
# Run the fail2ban-client, and generate the list of operating jails
# #####################################################################
-jail_list=$($fail2ban_client status|grep "list" |cut -f 3 |tr -d ,)
+jail_list=$($fail2ban_client status|grep "list" | cut -d : -f 2 | tr -d ,)
# #####################################################################
# Cycle through all jails, count blocked IP, and build output strings


 New Listings
New Listings